Introduction
Picture this: You're standing in front of a public terminal at the airport, trying to check your flight status, when suddenly someone's grandmother starts trying to install Candy Crush on it. Sound familiar? That's exactly why kiosk mode exists - to save us all from the chaos of unrestricted public devices!
Think of kiosk mode as putting your device in a digital straightjacket - but in a good way! It's like having a bouncer for your computer that only lets one specific app into the VIP section.
Perfect Use Cases
This streamlined approach uses Intune's built-in kiosk policies and Settings Catalog for a simplified deployment process - because who has time for complicated configurations when there are devices to manage and coffee to drink?
Step 1: Configure Auto Logon
Setup Process
-
1
Download the Autologon Tool from Microsoft Sysinternals.
-
2
Launch
Autologon.exeas Administrator. -
3
For Entra ID joined computers, configure:
- Username: [email protected]
- Domain: AzureAD
- Password: user password
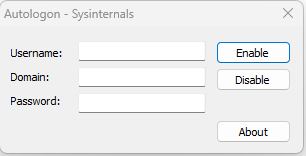
AutoLogon Configuration
Technical Insight
This utility writes the credentials to the registry in a secure manner under HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon.
This enables seamless user login on boot. For Entra ID joined devices, the domain must be specified as "AzureAD" to properly authenticate against the cloud directory.
Step 2: Disable InPrivate Browsing
Settings Catalog Configuration
- 1 Navigate to Devices > Configuration in Intune
- 2 Click Create > New Policy
-
3
Select configuration:
- Platform: Windows 10 and later
- Profile type: Settings Catalog
- 4 Search for and add "Configure InPrivate mode availability (User)"
- 5 Set to "InPrivate mode disabled"
Technical Implementation
This Settings Catalog policy leverages Microsoft Edge Administrative Templates via the Windows Policy CSP. Intune sends SyncML commands targeting the Policy CSP with OMA-URI targeting registry keys under HKLM\SOFTWARE\Policies\Microsoft\Edge.
Step 3: Create the Kiosk Policy
Policy Creation Steps
- 1 Navigate to Devices > Configuration in Intune
-
2
Select configuration:
- Platform: Windows 10 and later
- Profile type: Templates
- Template: Kiosk
-
3
Configure kiosk settings:Mode: Single app, full-screenLogon: Microsoft Entra userApp: Microsoft Edge BrowserURL: Your target websiteMode: Public Browsing (InPrivate)Refresh: 30 minutes idle
Behind the Scenes
This template utilizes the AssignedAccess CSP to configure single-app kiosk mode. Intune generates SyncML payload targeting ./Device/Vendor/MSFT/AssignedAccess/Configuration.
The CSP creates a restricted shell environment with application allowlisting at the kernel level.
Critical Security Warning
Important: Microsoft's documentation clearly states that "The kiosk profile doesn't load for members in the local admin group." Adding kiosk users to the local administrators group defeats the security purpose of kiosk mode and should be avoided in production environments.
Handling Software Restriction Errors
If you encounter software restriction errors, consider these secure alternatives instead of making the user a local administrator:
Option 1: App-Specific Allowlisting (Recommended)
- 1 Navigate to Intune > Devices > Configuration > Create Policy
- 2 Select Windows 10 and later > Templates > Windows Defender Application Control
- 3 Configure specific application exceptions for required diagnostic tools
Option 2: Custom OMA-URI Configuration
Use a custom OMA-URI to modify the AssignedAccess configuration:
OMA-URI: ./Device/Vendor/MSFT/AssignedAccess/Configuration
Data Type: String
Value: [XML configuration with specific app allowlist for diagnostic tools]Option 3: Breakglass Account (Emergency Access)
Create a separate break-glass local administrator account for maintenance:
# Create break-glass admin account (run as administrator)
net user kioskadmin ComplexPassword123! /add
net localgroup Administrators kioskadmin /add
net user kioskadmin /active:no
# Enable only when needed for diagnostics
net user kioskadmin /active:yesReal-World Implementation Experience
Authors' Note
Practical Reality: Despite our best efforts to implement kiosk mode following security best practices, we encountered persistent software restriction errors that prevented the kiosk from functioning properly. We attempted multiple approaches including custom OMA-URI configurations, application allowlisting policies, and Windows Defender Application Control settings.
After extensive testing and troubleshooting, none of the secure alternatives worked reliably in our environment. Given that our kiosk workstations are deployed exclusively within secured office premises (not public-facing), we made the pragmatic decision to use the local administrator approach as an acceptable risk trade-off.
Lesson learned: Sometimes theoretical best practices need to be balanced against real-world implementation constraints and risk tolerance.
Diagnosing Software Restriction Errors
When you encounter software restriction errors in kiosk mode, follow this systematic diagnostic approach:
Step 1: Identify the Error Source
Check these primary locations for error details:
# Check Windows Event Logs
Get-WinEvent -LogName "Microsoft-Windows-AppLocker/EXE and DLL" | Where-Object {$_.LevelDisplayName -eq "Error"} | Select-Object TimeCreated, Id, LevelDisplayName, Message
# Check Application Event Log
Get-EventLog -LogName Application -Source "Application Error" -Newest 10
# Check System Event Log for kiosk-related errors
Get-EventLog -LogName System | Where-Object {$_.Message -like "*kiosk*" -or $_.Message -like "*assigned*"} -Newest 10Step 2: Analyze AssignedAccess Configuration
Verify the current kiosk configuration:
# Check current AssignedAccess configuration
Get-AssignedAccess
# View detailed kiosk configuration
Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\AssignedAccessManagement\AssignedAccessSettings" | Format-List
# Check for conflicting policies
Get-AppLockerPolicy -Effective | Format-List
# Verify user account configuration
whoami /groups
net user $env:USERNAMEConclusion
This comprehensive approach to implementing kiosk mode via Intune demonstrates the sophisticated underlying technologies that power modern device management. Understanding the SyncML protocol, CSP architecture, and OMA-DM standards provides administrators with the knowledge needed to troubleshoot issues and implement advanced customizations.
Security Features
- Container Isolation
- AppLocker Integration
- File System Redirection
Best Practices
- Staged rollouts to pilot groups
- Proper monitoring procedures
- Documentation maintenance
